Understanding the Google Chrome 46 Connection Tab

On October 13, 2015, Google released Chrome 46. Chrome 46 introduces an icon change in the URL address bar for sites with minor HTTPS connection errors. Minor errors include a lack of Certificate Transparency (CT) information and/or use of SHA-1 certificates, obsolete cipher suites, and certain types of mixed content.
In an effort to encourage site operators to move over to HTTPS and SHA-2, Chrome 46 will display the “neutral page icon” instead of the (previously used) yellow triangle icon.
Google did this to help users and site operators by reducing the number of signs Internet users need to remember. The change gives users a better indication of a site's level security. Site operators benefit because they will no longer have to worry about the yellow triangle icon in the URL address bar that may suggest to users that the site is less secure. Instead, site operators can focus efforts on taking the necessary steps to make the site(s) more secure.
The below information is accurate for Chrome versions 45 and 46.
Connection Tab Warnings and Fixes
The yellow triangle or red 'X' icons in Google Chrome’s "Connection" Tab are alarming and can be difficult to understand. Below are four brief explanations about what causes the warnings and some tips for resolving related problems.
Certificate Transparency Information
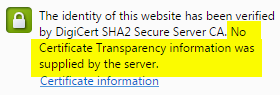
The identity of this website has been verified by DigiCert SHA2 Secure Server CA. No Certificate Transparency information was supplied by the server.
The first paragraph in the Connection Tab identifies whether a certificate has been logged in a public audit record. The public audit records Chrome uses and what is referred to in the Connection Tab is Certificate Transparency (CT). CT is still in its infant stages, so most sites will not have it enabled. Hopefully, this will change as CT becomes required for more types of digital certificates.
CT information is currently required only for Extended Validation (EV) SSL Certificates issued after January 1, 2015. CT information is not required for Organization Validated (OV) or Domain Validated (DV) SSL Certificates.
The Fix
All DigiCert EV SSL Certificates have CT enabled by default. If you are a DigiCert customer and would like to enable CT for your account, contact our support team. If you’re not a DigiCert customer, simply contact your Certificate Authority (CA) to see what they can do for you.
SHA-1
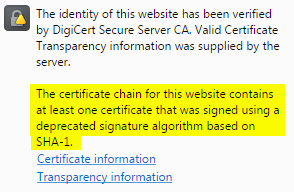
The certificate chain for this website contains at least one certificate that was signed using a deprecated signature algorithm based on SHA-1.
If you are seeing a warning icon in the first section of the Connection Tab, it is likely due to the presence of a SHA-1 certificate.
A yellow triangle typically means that your SSL Certificate expires between January 1, 2016, and January 1, 2017, and also has a SHA-1 certificate in the certificate chain.
A red 'X' generally means that your SSL Certificate expires after January 1, 2017, and there is a SHA-1 certificate in the certificate chain.
The Fix
If your SSL Certificate is SHA-1 or is issued off of a SHA-1 intermediate certificate, then you need to reissue it to SHA-2. If your certificate is through a different CA, you can reissue your certificate as SHA-2 for free through DigiCert’s SHA-1 Sunset Tool.
If there is an extra cross-chained SHA-1 root certificate in the chain, then you will most likely need to remove it. Click here to remove the SHA-1 certificate from your server, and click here to resolve the issue on your browser.
Obsolete Cipher Suite
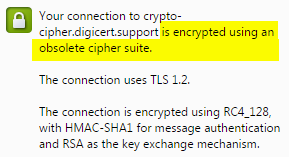
Your connection to example.com is encrypted using an obsolete cipher suite.
There are two reasons this warning may appear: One reason is caused by the cryptographic protocol being used. The other reason is due to the cipher suites that are enabled.
TLS
The warning message will appear if TLS 1.2+ is not supported.
Cipher Suites
The warning message will also appear if insecure cipher suites (e.g., RC4) are enabled.
The Fix
TLS
Enable support for TLS 1.2+.
Insecure Cipher Suites
Enable secure cipher suites (AES_128_GCM). If you are using deprecated cipher suites for backwards compatibility then you need to prioritize AES_128_GCM over the other cipher suites.
DigiCert Certificate Inspector is a free tool you can use to discover which cipher suites you have enabled on your servers.
Mozilla maintains a “best practices” guide for configuring Server Side TLS.
Mixed Content
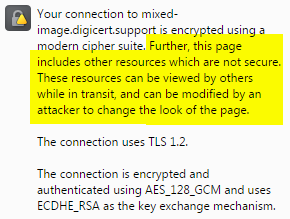
Further, this page includes other resources which are not secure. These resources can be viewed by others while in transit, and can be modified by an attacker to change the look of the page.
If a website is secured with a SSL Certificate, but it pulls content from connections that are not encrypted (HTTP), then the site is considered to have mixed content. If you open the console in your browser (F12) on a page where you see mixed content warnings, the browser will typically report what resources are causing this warning.
The Fix
All unsecure resources need to be moved over to a HTTPS connection. Most popular resources (i.e. social media widgets, embedded videos and images, fonts, APIs) are available over HTTPS. To move them over, update your HTML to request those resources from the HTTPS address instead of HTTP.