Understanding the Differences Between Leaders and Laggards in PKI Automation
Last time, in Enterprises Overwhelmed In The Absence Of PKI Automation, DigiCert Finds, we began to explore a survey where DigiCert found that the number of certificates had increased for most organizations in recent years. The DigiCert PKI Automation study also uncovered that many organizations had suffered a certificate outage because of limited visibility. This explains organizations’ ongoing move towards PKI automation.
What PKI automation entails
Lots of different factors are driving organizations’ shift to PKI automation. Before we get into that, however, we first need to classify what automation is. So when customers say they want automation, what comes to mind is installing a cert on a server as well as wanting to find the cert no matter where it is and how it fits into the environment. Lots of things contribute to that process, and once their teams find it, organizations want to inventory, manage and see it.
But that brings organizations into a notification bucket. They’re not going to log into their dashboard every day, and things are always changing. Acknowledging that, organizations really need some way that keeps detecting, keeps finding, keeps dumping relevant information into a central repo, and keeps notifying them of changes through the appropriate channels. Those venues don’t include email. Instead, they need to connect to an ITMS system, Splunk or operational system that goes through change control and that drives change through the environment. Change could require manual intervention, after all, or maybe organizations are looking for that last piece of automation where they need to generate a key per their policy and specs. The whole certificate lifecycle is at play here.
PKI automation therefore accounts for a dynamic landscape where people want to control and manage things. That’s what stands out with customers. It’s about discovery, management/reporting, notification, automation (using privileged access management or vault), and then CA integration and importing of third-party CA or certs.
How do organizations feel about PKI automation?
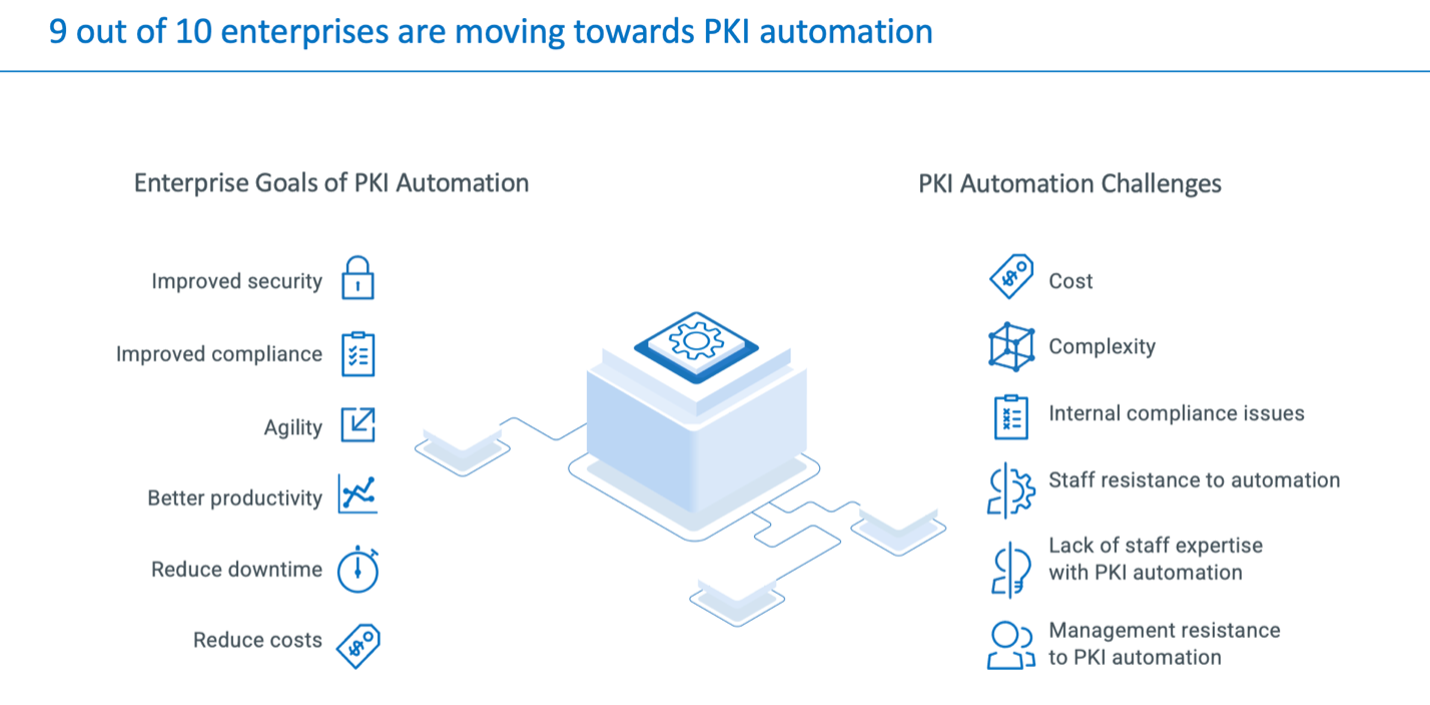
When asked about how they feel about PKI automation, most organizations expressed enthusiasm. More than nine in 10 (91%) of respondents to DigiCert’s survey said that they’re at least discussing PKI automation. What’s more, 70% of survey participants said that they expected to implement a PKI automation solution within 12 months, while just under a quarter (24%) said they were at a stage where they were already in the process of implementing a solution or where they had already implemented a solution.

DigiCert’s 2021 State of PKI Automation Survey
That brings us to the trends driving organizations to adopt PKI automation. Chief among those factors are rogue certificates. This problem used to be the case where someone in IT started up a certificate to solve a point problem and things got out of control. That left organizations with the need to figure out how to manage the issue.
Rogue certificates are a different problem today. They still arise, but they’ve expanded because PKI is being used on everything. Certificates can protect a router or a switch that comes with its own PKI system. When organizations get several of those same devices together, for instance, they can use the PKI system to sign certificates for traffic going through them. Lots of technology comes with self-contained PKI in this way. So too do software environments. (Here’s looking at you, DevOps.) All these ingress points of hardware, software and services create a burden for organizations to manage their certificates.
Rogue certificates aren’t the only factor that’s driving PKI automation. Organizations also need to be ready when quantum computing becomes mainstream and when it forces enterprises to quickly change out encryption methodologies. There are also shrinking certificate validity periods for publicly trusted TLS, rapid increases in the number of certificates that need to be managed, and the ongoing shift to remote work that’s helping to propel these trends.
PKI automation as a spectrum
Some organizations are experiencing challenges in their automation journeys. Those obstacles include a high cost to automate, complexity, issues with compliance, as well as staff and management resistance to change.
DigiCert’s 2021 State of PKI Automation Survey
How organizations respond to those challenges in turn differentiates them as leaders, laggards or somewhere in the middle of PKI automation.
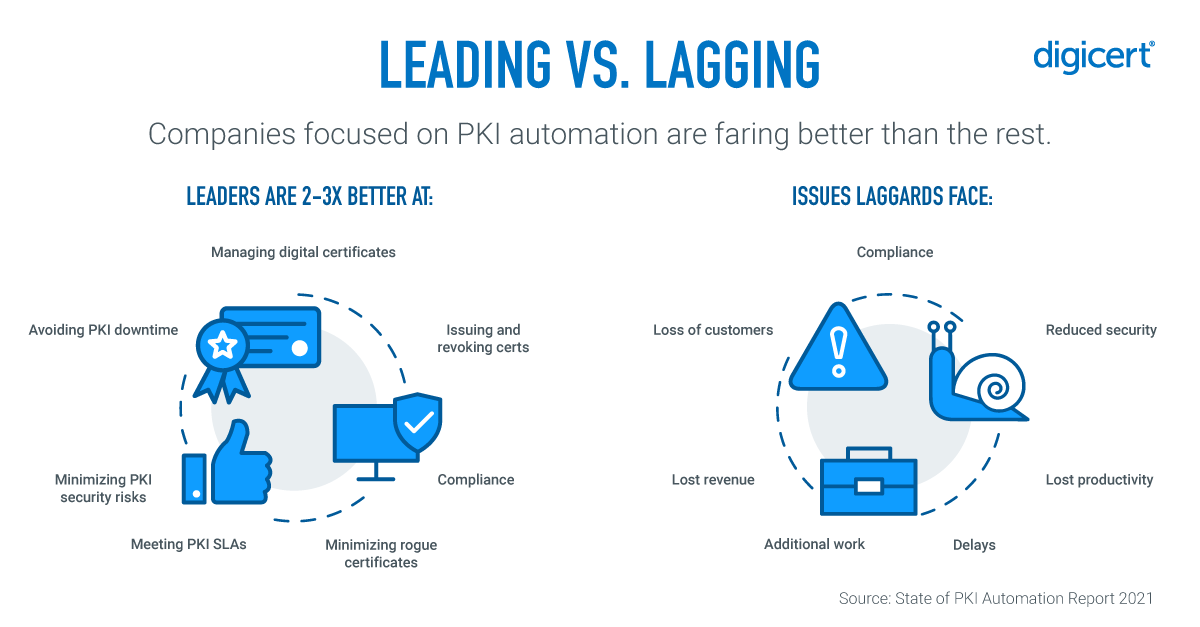
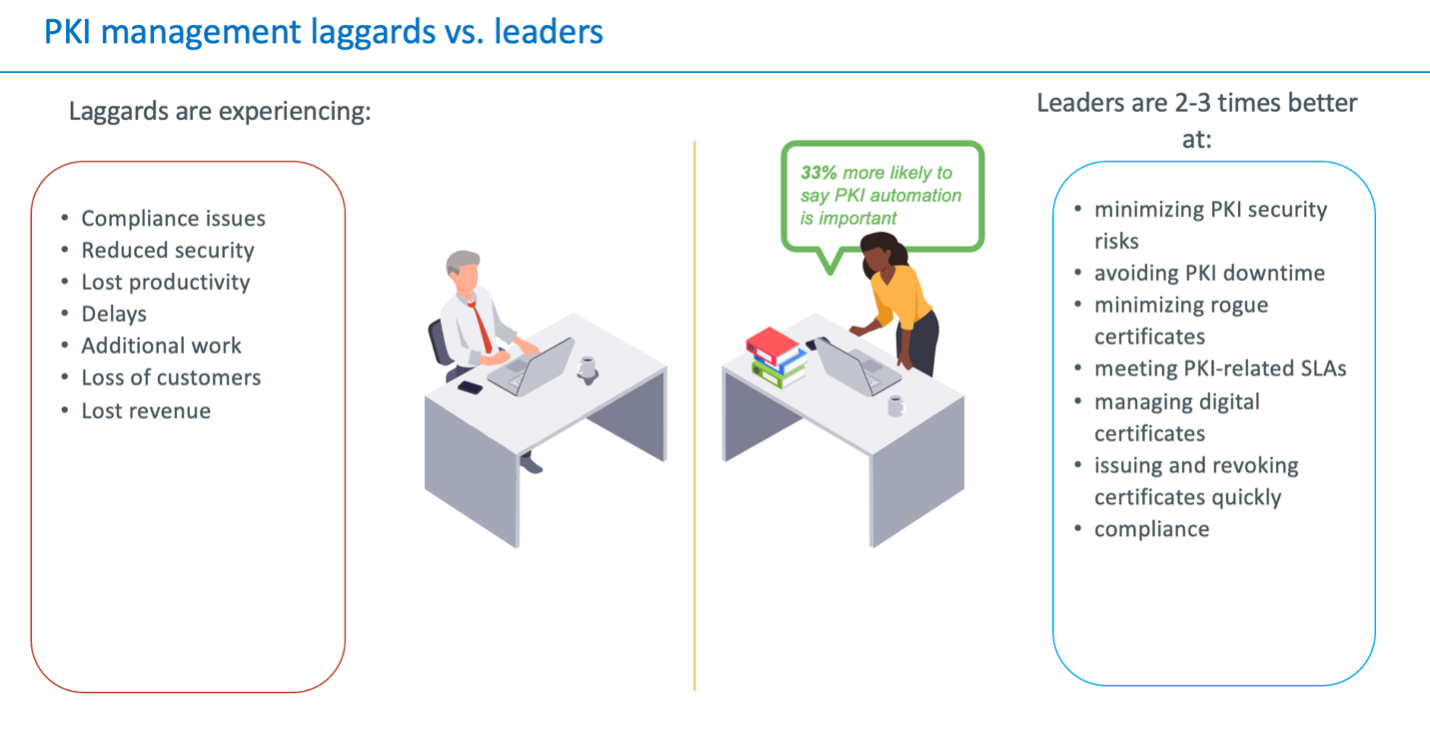
What separates a leader from a laggard? Leaders characteristically have processes in place for managing how things are coming into their infrastructure. These processes include mature security operations for vetting and taking care of their IT assets, with PKI just one element. Downstream from that, leaders have also looked at how to automate and manage crypto. They therefore have a corporate policy around crypto, a framework that they’re using for trying to reduce things like key sharing, bad algorithms, untrusted algorithms and weak key sizes. They’re also concerned about rogue certificates and the time it takes to manage PKI certificates, making them even more likely to have already implemented a PKI automation solution.
DigiCert’s 2021 State of PKI Automation Survey
By contrast, laggards lack in at least two to four of those categories. They experience penalties for their lack of skill in managing PKI certificates. These outcomes include compliance issues, security issues, lost productivity, delays, lost customers, lost revenue and a state of being overworked.
Drawing to a close
In our third and final installment of this series, we’ll share some interesting trends that stood out to DigiCert in its survey.
The digital world is turning into a sprawling mesh of connection points. Learn more about how to unify and simplify your expanding security environment in our new webinar. Register now.







