History serves as an early warning system. Cyberwars are as old as the internet itself and originated with simple tools designed to exploit vulnerabilities in operating systems, applications and network services. In 1988 they landed as viruses through portable media and spread over the network as worms. By 2010, they acquired broadcast capability as botnets. In 2012 they were referred to as complex malware. They continued their evolution from tools to smart weapons. By 2015, they transformed into advanced persistent threats (APTs) and kill chains.
Protecting devices in the age of cyberwarfare will literally require drawing the line in the sand between the traditional information technology (IT) and operational technology (OT) wheelhouses.
The emerging landscape of cyberwarfare
Today they are staged as coordinated cyberattacks on critical infrastructure and as mainstream ransomware operated by sophisticated nation-state actors with weaponized cryptography, targeting the soft core in critical infrastructure. Malware is transforming in the sophistication of network surveillance and lateral propagation from the demilitarized zone (DMZ) to controllers, actuators and sensors. Industrial brownfield and greenfield devices lack cyber resilience by design and are unprepared for the emerging wave of cyberattacks.
The root cause is that hackers know how to evade detection and prevention controls. IT security was designed for network traffic introspection — with rules-based firewalls, threat intelligence, and policy grammar-based intrusion and anomaly detection. Retrofitting IT countermeasures in OT is fundamentally flawed because the vulnerabilities in devices and humans are radically different. The behavior of devices is deterministic, whereas human psychology is hard to comprehend. Protecting devices requires a horizontal platform of transitive trust and a vertical pillar of integrated trust.
The top five industry trends
- Digital transformation
The first (top) emerging trend, digital transformation, in the context of devices may be summarized in one sentence: Artificial intelligence (AI) drives machine learning (ML) to achieve operational efficiency, with digital privacy and data protection, to enable data sharing. AI requires both network and device intelligence for continuity and runtime integrity of mission critical services in automation powered industrial applications. ML provides operational efficiencies through observations for evidence-based abductive reasoning models, condition-based maintenance for longevity of service life, and telemetric measurements for quality improvements and design innovations.
2. Zero trust
The second emerging trend is the zero-trust model. Fundamentally, this boils down to a volume, velocity and variety challenge for real-time, low-latency line of business (LOB) applications. The volume refers to heterogeneous devices, cryptographic keys and certificates for device identification and authentication. Velocity entails protective measures that require automation for transfer of ownership, key and certificate lifecycle management. The variety of cryptographic algorithms (in a global and fragmented market with export/import controls) requires an abstraction layer and restricted key usage.
3. Trust in the supply chain
The third emerging trend is building trust in the supply chain. The attack surface is elastic and has many blind spots from the silicon fab lab to original equipment manufacturers (OEMs), device owners, device operators and the heterogeneous set of connected brownfield and greenfield devices. A horizontal trust chain is required beginning at the root of trust, with manufacturer and device owner issued identifiers, and cryptographic key usage based on the principle of least privilege. Most importantly, it requires a hosting platform and certificate authority (CA), without cloud platform or CA lock in, for ease of migration and cost management.
4. Digital twins, driven by AI initiatives
The fourth emerging trend is digital twins driven by AI initiatives, for quality improvements and design innovation based on telemetric datasets and synchronization of state. This will require plugging security gaps between the virtual and physical systems; preventing compromise of the virtual digital twin by hackers to expose the internal view of the actual physical system; achieving event-based synchronization with regular transfer of accurate and tamper-resistant data with low latency; synchronizing the configuration state for trustworthiness with platform attestation; and synchronizing software updates with supply-chain provenance for preservation of functional and cycle accurate equivalency.
5. Secure by design
The fifth emerging trend is application security by design. LOB applications must address compliance requirements and risk management objectives, from resource constrained sensors and actuators to controllers and edge gateways for outreach into cyberspace. Such objectives must include protective controls for data privacy, data protection, device authentication, integrity monitoring and remote recovery.
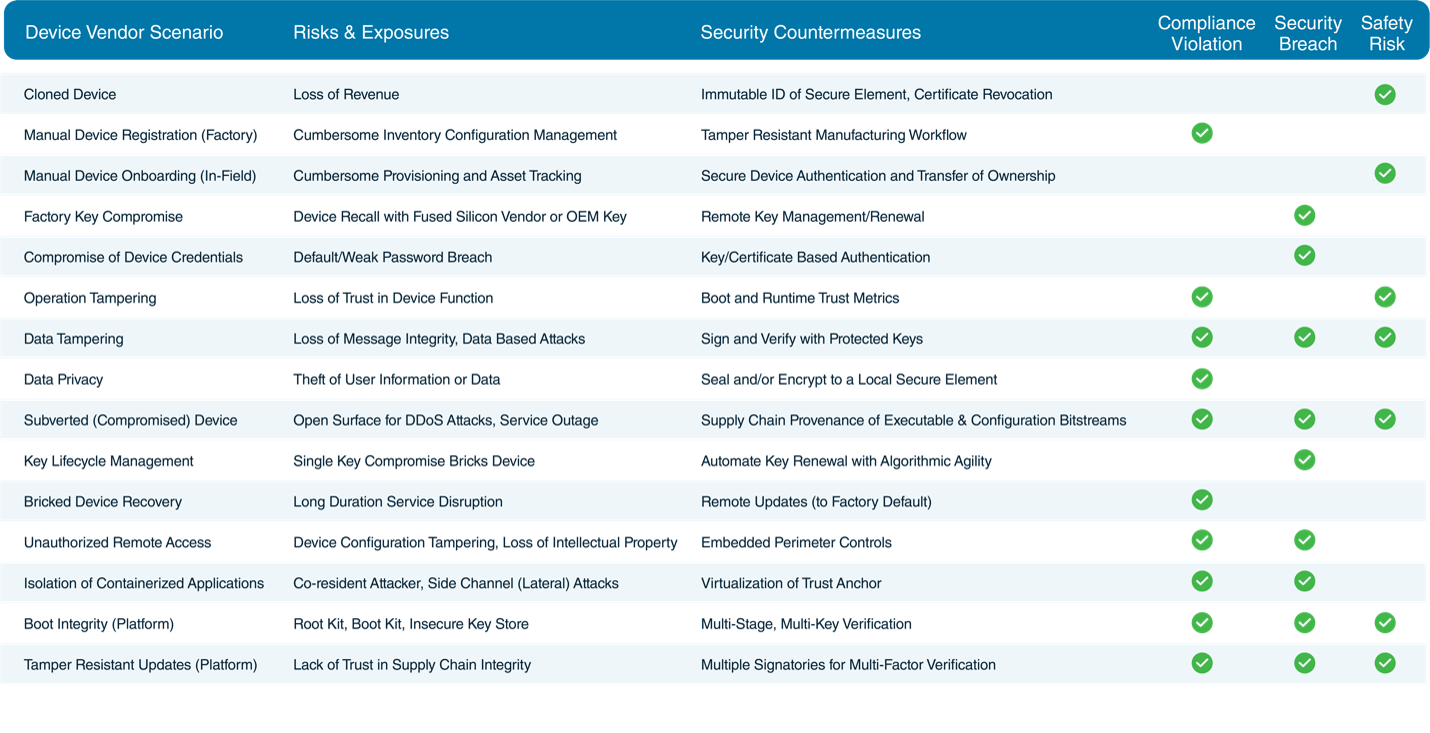
Threats versus risks (knowing the difference)
The risk model in OT is based on compliance, security and safety considerations. Each risk, unlike threats, has a tangible cost and benefit metric. For example, a factory key compromise may require a device recall or truck roll to remediate; a device bricked by ransomware may cause long duration service outage; a rootkit or boot-kit infection may require manual intervention with a factory reset to recover.
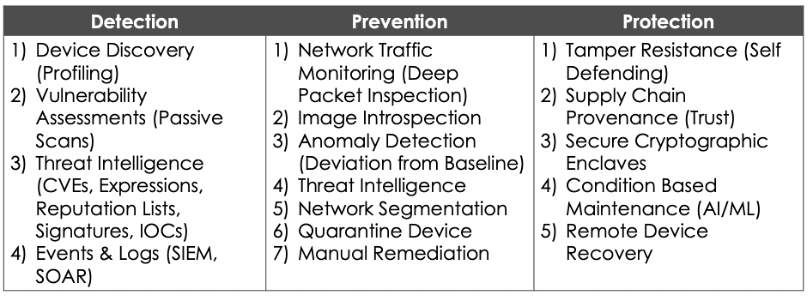
Protection versus detection: understanding the difference
The detection and prevention tools and methods that hackers are well-versed in, the volume of events with low signal-to-noise ratio, and the cost of post-breach forensics to generate threat intelligence is a strategy that is not sustainable. Hackers are two steps ahead of expert systems. They have the first-strike advantage.

The detection and prevention countermeasures provide policy and rules-oriented grammar for visibility. However, risk controls require embedded protection-oriented countermeasures with tamper resistance, supply-chain trust and cryptographic enclaves. Why? Because risk mitigation requires condition-based maintenance, remote device monitoring and recovery.
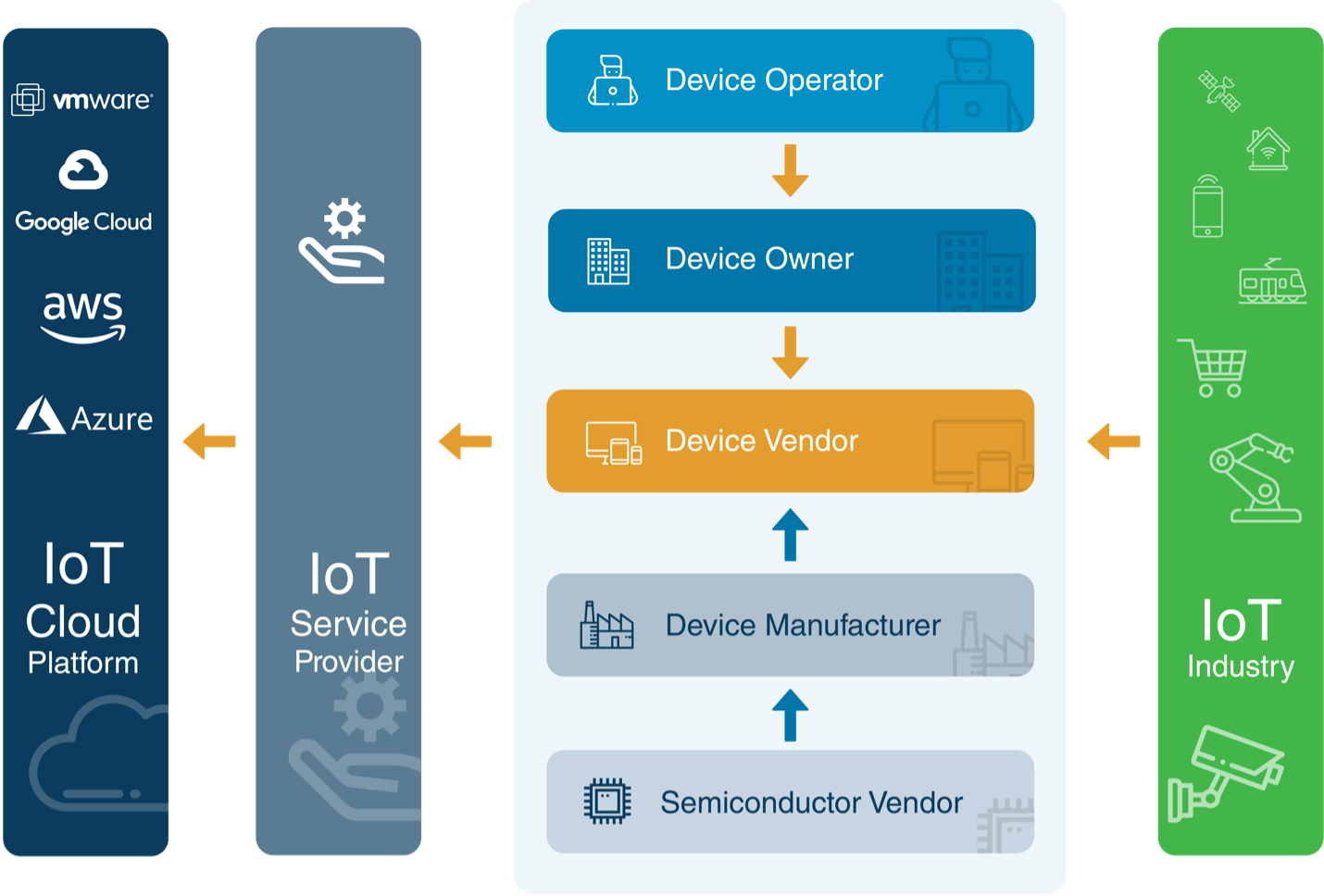
IT/OT convergence requires an ecosystem fit and finish
The IoT ecosystem, workflows and underlying technologies require a collaborative mindset from the silicon vendor to the manufacturers, operators and service providers. The convergence of IT and OT ecosystems requires alignment.
OT security is the fusion of network operations center (NOC), security operations center (SOC), device management systems (DMS) and application management systems. SOC operators require supply-chain tamper resistance, device intelligence and indicators of risk for remote maintenance and recovery of OT devices.
DMS operators require authenticated device identifiers for secure onboarding, on-device protection of cryptographic artifacts, secure boot sequence and data diode mode of operation for integrity monitoring.