
Hackers will take advantage of any vulnerability they can find. Amidst the pandemic of COVID-19, attackers are taking advantage of the alertness of the world population with phishing emails, social media posts, apps and text messages containing malware. These scams typically involve fraudsters impersonating healthcare officials.
According to Check Point Threat Intelligence, “since January 2020, there have been over 4,000 coronavirus-related domains registered globally. Out of these websites, 3% were found to be malicious and an additional 5% are suspicious. Coronavirus- related domains are 50% more likely to be malicious than other domains registered at the same period.”
In fact, the United States Cybersecurity and Infrastructure Security Agency is advising individuals to exercise caution with any email or social media post with a COVID-19 related subject line, attachment or link. Some attackers have even created apps claiming to have information on COVID-19 which, once downloaded, can lock out users until a ransom is paid.
As these cyberattacks continue to spread, use these six best practices to help protect yourself.
Check for Common Signs
If a form of communication asks you to click a link, download an attachment or give any personal or financial information, this should be a red flag. Do not exchange information or do financial transactions with entities that you are not familiar with.
Look for common signs of fraudulent sites/ emails including:
- Poor design
- Poor grammar or spelling
- Unreliable contact information
- No Terms and Conditions listed
- Deals that seem too good to be true
- Suspicious forms of payment (like sending money to a random PayPal account)
Treat Emails About COVID-19 with Suspicion
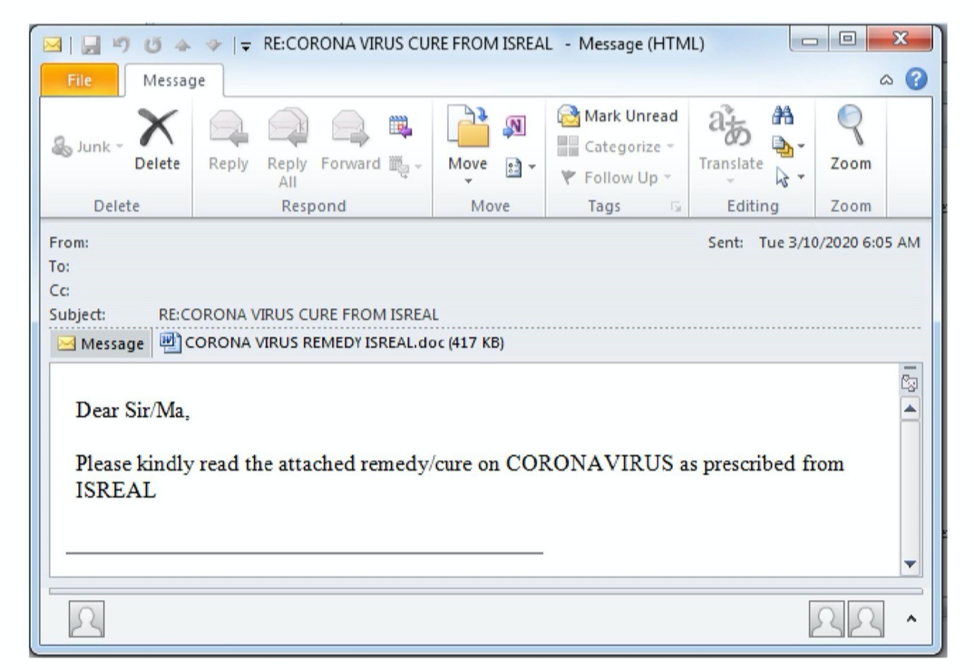
This sample phishing email lures readers in with a “cure” to the virus, but the attachment contains malware. Reading carefully reveals that the fraudster spelled Israel “Isreal,” which is a clear red flag.
Pay Attention when Browsing
It’s also important to be careful when browsing, whether on websites, social media or apps. You can check the sites you visit for TLS (Transport Layer Security) /SSL (Secure Sockets Layer), the standard technology for keeping an internet connection secure and safeguarding any sensitive data that is being sent between two systems. Different browsers have unique identifiers to show if a website is secure. View our blog on how to identify authorized sites to know how to distinguish authorized from unsecured sites.
Additionally, web users can check the safety of a site by copying and pasting the URL into the Google Safe Browsing Transparency Report. If a suspicious or fraudulent site is found, it can be reported to Google’s Safe Browsing or Mozilla’s Protect the Fox.
Don’t Download Unknown Attachments (Like This Map)
Malware is currently spreading through cybercriminals distributing via email a map similar to the one by Johns Hopkins University. The map often includes links to malicious sites disguised as official communication.
Beware Text Messages Claiming to be from the CDC
Reports of people receiving a text message from the CDC have surfaced, but they are a hoax. In general, do not click on links in text messages from unrecognized numbers. They can link you to sites that distribute malware.
Fight Technology with Technology
To prevent attacks always update your software and browser with the latest versions of Microsoft Edge, Mozilla Firefox and other vendors' browsers that come equipped with anti-phishing filters.
Existing technologies such as PKI (Public Key Infrastructure), which provides encryption and cryptographic identity guarantee in each data flow and verifies all network users, can play a key role in protecting homes, businesses and connected networks. Email attacks are common forms of phishing and social engineering, and companies can also help protect users and other people who trust their email systems by using digital certificates to assure the identity and authentication and encryption of the client.
Overall, rely on legitimate health services and government websites for information. Do not give out personal or financial information and verify that a charity is legitimate before making donations. You may want to review the FTC guidelines for vetting a charity and avoiding scams before making any donations.
During this global pandemic, not only do we need to reexamine our social habits, but also our digital ones. Following these tips can protect against hacker attacks and data leakage, keeping your network and devices safe.







