
Best practices to help your organization send and receive secure messages
How many emails do you receive every day? How do you know the emails you are sending and receiving are secure? How do you know that your employees’ emails are secure, especially when they are working remotely and sending emails from home or unknown locations?
Furthermore, how do users know that an email is actually from your organization? When a hacker pretends to be from an organization, it not only costs companies millions of dollars each year but also damages trust between a company and its customers. Building trust through secure email access is critical to ensuring that information remains secure and private.
To combat compromised email attacks, several protocols were created. These, combined with other best practices, can help your organization secure your remote workforce’s email. This is especially important as attackers are currently spoofing emails and messages to take advantage of the current global crisis. For example, some malware was spread in March through an email attachment spoof of the John Hopkins University map.
1. Use S/MIME (Secure/Multipurpose Internet Mail Extensions) protocol
S/MIME is a method for sending digitally signed and/or encrypted messages. Using S/MIME in email reassures receivers that the message in their inbox is the exact same message from the sender. It also validates the identity of senders, so receivers know that the message is coming from the real sender and not an imposter. Thus, S/MIME provides authentication, message integrity, privacy and data security.
Within organizations, your IT department will be responsible for setting up S/MIME by providing digital certificates to users or by using a third-party platform to enforce security on email messages.
For non-corporate users, you would need to obtain a digital certificate from a certificate authority to enable S/MIME. Then you must follow the instructions to install that certificate in your email client (i.e. Outlook).
Once you set up S/MIME, you will need to do a one-time exchange of digitally signed emails with the recipient. This will then allow you to send encrypted emails.
Google Gmail supports a few different secure email methods as outlined in this support article: Gmail Help. Here’s an example of what secure email looks like in your Gmail inbox:
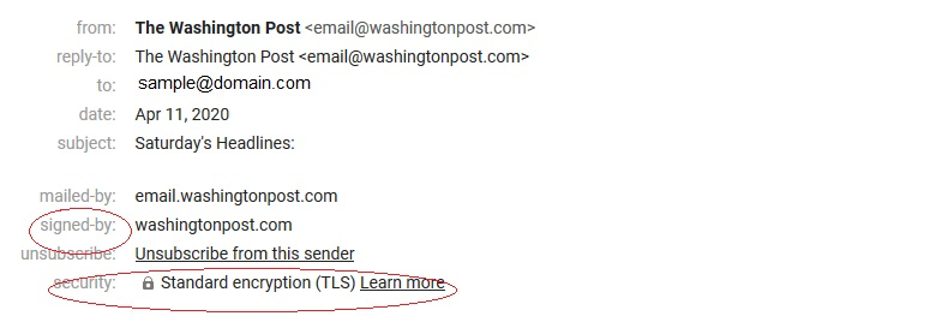
Note that this is not end-to-end encryption as you would get with S/MIME rather messages are encrypted between email servers.
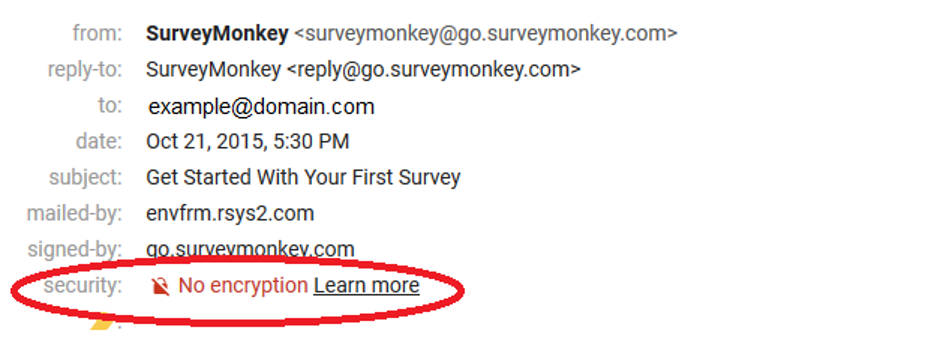
If an email doesn’t have encryption, it will say “no encryption”.
2. Work towards DMARC certification
DMARC (Domain-based Message Authentication, Reporting and Conformance) ensures that others cannot pretend to be from a legitimate corporate domain so that your emails can’t be spoofed. For example, if an organization like PayPal has DMARC, then fraudsters cannot send emails from the PayPal domain because the receiving email provider will either quarantine or reject messages from unauthorized accounts. Thus, only authenticated messages are accepted into email users’ inboxes.
After your organization has this protocol, you can also configure alerts for your organization when an unauthorized email is sent from your domain, helping you increase visibility and monitor suspicious activities.
DMARC implementation requires that your organization inventory all domain senders authorized to send messages on behalf of your organization and whitelist them. Outsourcing emails to third-party senders can make this process more complicated, but it’s certainly doable.
A DMARC policy can be configured in three ways: none, quarantine or reject. When organizations initially create a DMARC record, they set the policy=none. But this wouldn’t result in any enforcement. Once the policy is set to quarantine or reject, they will see the benefit of DMARC. In 2018, the U.S. Department of Homeland Security issued a directive to get all U.S. government domains DMARC enforced (see https://cyber.dhs.gov/bod/18-01/). In record time, government domains implemented DMARC. Businesses should also work towards DMARC certification and enforcement to protect their brand from being used in false messaging.
3. Use a VPN for your workforce
A Virtual Private Network (VPN) adds a layer of security and privacy to email by encrypting traffic through a server, so it is more difficult for hackers to intercept it. Utilizing digital certificates for authentication to VPNs provides an extra layer of security for sensitive communication.
4. Look forward to BIMI
Brand Indicators for Message Identification (BIMI) is an email specification that enables brand-controlled, validated logos in supporting email providers. This emerging standard will build on DMARC authentication by displaying brand logos on email messages verified with DMARC. Logos will be validated by certificate authorities, who will issue Verified Mark Certificates. A pilot is planned for Q2 with general availability later this year. The first Verified Mark Certificate was issued by DigiCert to CNN in October 2019.
5. Remember email management best practices
On top of having good security tools, you should also do what you can to encourage employees to keep their email safe, especially when they are working remotely and cannot authenticate messages in person.
Organizations should implement and enforce a company-wide email policy if they do not already have one. For instance, close former employees’ email accounts so that they cannot access them and forward correspondence to a current employee. You may also consider offering security awareness training to employees since helping employees practice good security habits is just as important as implementing security protocols. Testing employee awareness with crafty emails to see if they click on suspicious links is a good way to ensure proper email hygiene.
In sum, securing your email, especially from home or unknown locations, helps to ensure the email content cannot be read by third parties and that the integrity of the message is intact.







