Use IIS 10 to export a copy of your SSL certificate from one server and
import and configure it on a (different) Windows Server 2016
Prevent email tampering and phishing with a DigiCert S/MIME certificate.
Buy NowWindows servers use .pfx files that contain both the public key file (SSL certificate file) and the associated private key file. When you generate the CSR, you create a key pair (public/private). You send the public key to DigiCert (a Certificate Authority), so we can create and issue your SSL certificate. The private key stays on the server you used to generate the CSR.
You need both the public and private keys for an SSL Certificate to function; therefore, if you need to transfer SSL server security certificates from one server to another, you need to create a .pfx backup and include the private key.
If you are looking for a simpler way to transfer your SSL certificates to your Windows server 2016, we recommend using the DigiCert® Certificate Utility for Windows. See Transferring a Copy of an SSL Certificate to Your IIS 10 Server.
To transfer a copy of an SSL certificate, do the following:
-
Use IIS 10 to export/back up the SSL certificate with private key as .pfx file from the Microsoft server where it's installed.
-
Use IIS 10 to import the SSL certificate with private key .pfx file to your (different) Windows server 2016.
-
Use IIS 10 to configure your Windows server 2016 to use the SSL certificate.
How to Configure Your Windows Server 2016 to Use the Imported SSL Certificate
I. How to Export/Back Up Your SSL Certificate w/Private Key
-
On the Windows server 2016 where the SSL certificate is installed, open the Console.
In the Windows start menu, type mmc and open it.
-
In the Console window, in the top menu, click File > Add/Remove Snap-in.

-
In the Add or Remove Snap-ins window, in the Available snap-ins pane (left side), select Certificates and then click Add >.
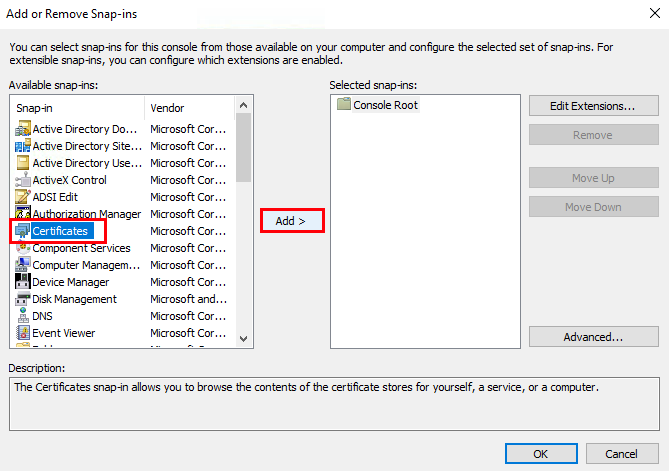
-
In the Certificate snap-in window, select Computer account and then click Next.

-
In the Select Computer window, select Local computer: (the computer this console is running on), and then click Finish.

-
In the Add or Remove Snap-ins window, click OK.

-
In the Console window, in the Console Root pane (left side), expand Certificates (Local Computer), expand the folder that contains the certificate that you want to export/back up, and then, click the associated Certificates folder.
Note: Your certificate should be in either the Personal or the Web Hosting folder.

-
In the center pane, right-click on the certificate that you want to export/back up and then click All Tasks > Export.
-
In the Certificate Export Wizard, on the Welcome to the Certificate Export Wizard page, click Next.
-
On the Export Private Key page, select Yes, export the private key, and then, click Next.

-
On the Export File Format page, select Personal Information Exchange – PKCS #12 (.PFX) and then check Include all certificates in the certification path if possible.
Warning: Do not select Delete the private key if the export is successful.

-
On the Security page, do following one of the following options:
Password: i. Check this box. Confirm password: ii. Then, create and confirm the password. Password Note: This password will be required when you import the certificate w/private key to your (different) Windows server 2016. Group or user name i. Check this box (recommended) ii. In the field below, select the Active Directory user or group account to which you want to assign access to the certificate w/private key. iii. Then, click Add. Export/Import Note: The server from which you export the certificate w/private key must be part of an AD domain. The server to which you import the certificate w/private key must be tied to an AD domain with a domain controller (DC). 
-
On the File to Export page, click Browse. In the Save As window, locate and select the certificate file that you want to export and then click Save. Finally, on the File to Export page, click Next.
Make sure to note the filename and the location where you saved your file. If you only enter the filename without selecting a location, your file is saved to the following location: C:\Windows\System32.

-
On the Completing the Certificate Export Wizard page, verify that the settings are correct and then, click Finish.

-
You should receive "The export was successful" message.
The SSL certificate w/private key .pfx file is now saved to the location that you selected.
II. How to Import the SSL Certificate w/Private Key .pfx File
If you have not yet exported the SSL certificate and its private key as a .pfx file from the server on which the certificate is installed, see How to Export/Back Up Your SSL Certificate w/Private Key.
-
On the Windows server 2016 where you want to install the SSL certificate, open the Console.
In the Windows start menu, type mmc and open it.
-
In the Console window, in the top menu, click File > Add/Remove Snap-in.

-
In the Add or Remove Snap-ins window, in the Available snap-ins pane (left side), select Certificates and then click Add >.

-
In the Certificate snap-in window, select Computer account and then click Next.

-
In the Select Computer window, select Local computer: (the computer this console is running on), and then click Finish.

-
In the Add or Remove Snap-ins window, click OK.

-
In the Console window, in the Console Root pane (left side), expand Certificates (Local Computer), right-click on the Web Hosting folder, and then click All Tasks > Import.

-
In the Certificate Import Wizard, on the Welcome to the Certificate Import Wizard page, click Next.
-
On the File to Import page, browse to and select the file that you want import and then, click Next.
Notes: In the File Explorer window, in the file type drop-down, make sure to select All Files (*.*). By default, it is set to search for X.509 Certificate (*.cert;*.crt) file types only.

-
On the Private key protection page, do the following:
Password: Type the password that you created when the SSL certificate was exported. Mark this key as Check this box so that you can back up or export the SSL certificate when needed. exportable. Note that a certificate without it's private key does not work. Include all extended Check this box. properties. 
-
On the Certificate Store page, do the following and then click Next:
-
Select Place all certificates in the following store and click Browse.
-
In the Select Certificate Store window, select Web Hosting and click OK.

-
-
On the Completing the Certificate Import Wizard page, verify that the settings are correct and then, click Finish.
-
You should receive "The import was successful" message.
The SSL certificate w/private key .pfx file is now saved to the Web Hosting store (folder).
III. How to Configure Your Windows Server 2016 to Use the Imported SSL Certificate
After you've imported the SSL certificate to your Windows Server 2016, you must configure IIS 10 to use the newly imported certificate to secure your website.
- (Single Certificate) How to configure the Windows server 2016 to use your SSL certificate
- (Multiple Certificates) How to assign your SSL certificates and configure the server to use them using SNI
(Single Certificate) How to configure the Windows server 2016 to use your SSL certificate
If you have not imported all your SSL certificates, see How to Import the SSL Certificate w/Private Key .pfx File.
-
On the Windows server 2016 where you imported your SSL certificate to, open Internet Information Services (IIS) Manager.
In the Windows start menu, type Internet Information Services (IIS) Manager and open it.
-
In Internet Information Services (IIS) Manager, in the Connections menu tree (left pane), expand the name of the server on which the certificate was installed. Then expand Sites and click the site you want to use the SSL certificate to secure.
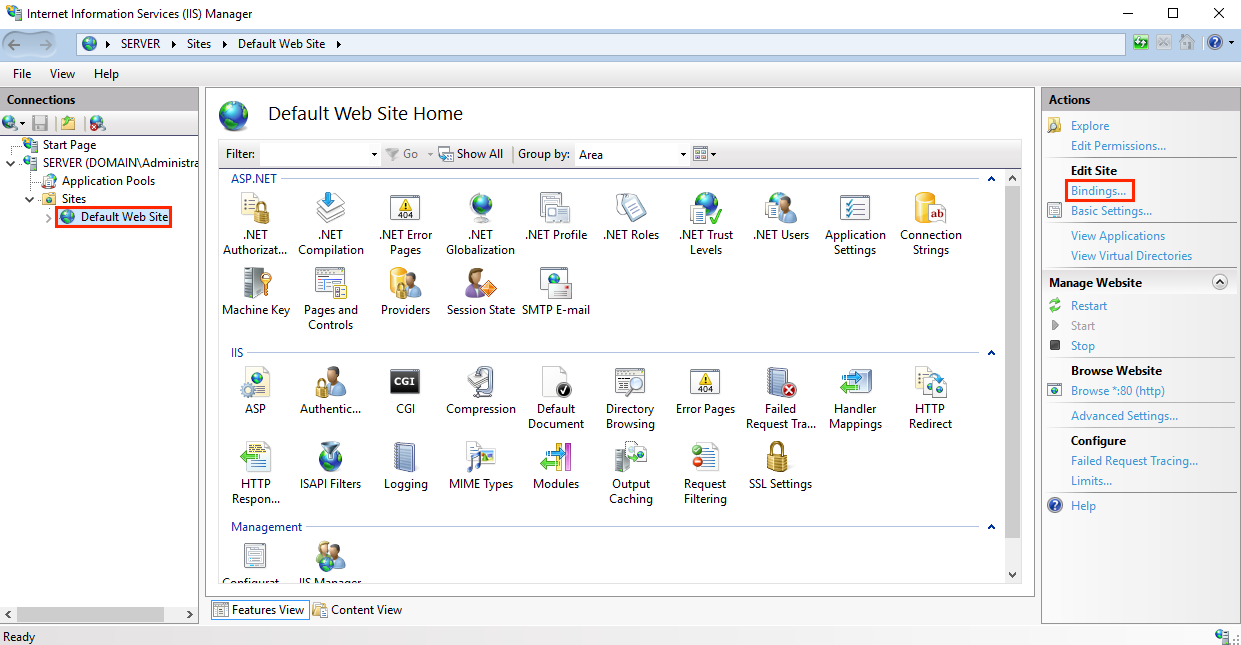
-
On the website Home page, in the Actions menu (right pane), under Edit Site, click the Bindings… link.
-
In the Site Bindings window, click Add.
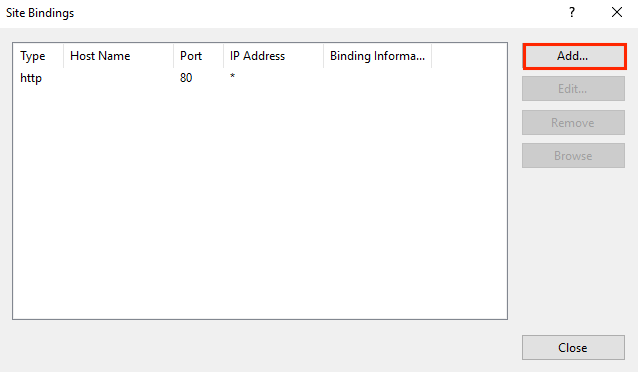
-
In the Add Site Bindings window, do the following and then click OK:
Type: In the drop-down list, select https. IP address: In the drop-down list, select the IP address of the site or select All Unassigned. Port: Type port 443. The port over which traffic is secured by SSL is port 443. SSL certificate: In the drop-down list, select your new SSL certificate (e.g., yourdomain.com). 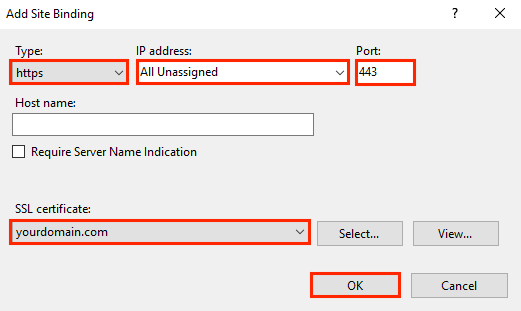
-
Your SSL certificate is now installed, and the website configured to accept secure connections.
(Multiple Certificates) How to assign your SSL certificates and configure the server to use them using SNI
If you have not imported all your SSL certificates, see How to Import the SSL Certificate w/Private Key .pfx File.
This instruction explains how to assign multiple SSL certificates using SNI. The process is split into two parts as follows:
Assign the First SSL Certificate
Do this first set of instructions only once, for the first SSL certificate.
-
On the Windows Server 2016 where you imported your SSL certificate to, open Internet Information Services (IIS) Manager.
In the Windows start menu, type Internet Information Services (IIS) Manager and open it.
-
In Internet Information Services (IIS) Manager, in the Connections menu tree (left pane), expand the name of the server on which the certificate was installed. Then expand Sites and click the site you want to use the SSL certificate to secure.

-
On the website Home page, in the Actions menu (right pane), under Edit Site, click the Bindings… link.
-
In the Site Bindings window, click Add.

-
In the Add Site Bindings window, do the following and then click OK:
Type: In the drop-down list, select https. IP address: In the drop-down list, select the IP address of the site or select All Unassigned. Port: Type port 443. The port over which traffic is secure by SSL is port 443. SSL certificate: In the drop-down list, select your new SSL certificate (e.g., yourdomain.com). 
-
Your first SSL certificate is now assigned, and the website configured to accept secure connections.
Assign All Additional SSL Certificates
To assign each additional SSL certificate, repeat the steps below, as needed.
-
In Internet Information Services (IIS) Manager, in the Connections menu tree (left pane), expand the name of the server on which the certificate was installed. Then expand Sites and click the site you want to use the SSL certificate to secure.

-
On the website Home page, in the Actions menu (right pane), under Edit Site, click the Bindings… link.
-
In the Site Bindings window, click Add.

-
In the Add Site Bindings window, do the following and then click OK:
Type: In the drop-down list, select https. IP address: In the drop-down list, select the IP address of the site or select All Unassigned. Port: Type port 443. The port over which traffic is secure by SSL is port 443. Host name: Type the host name that you want to secure. Require Server After you enter the host name, check this box. Name Indication: This is required for all additional certificates/sites, after you've installed the first certificate and secured the primary site. SSL certificate: In the drop-down list, select an additional SSL certificate (e.g., yourdomain2.com). 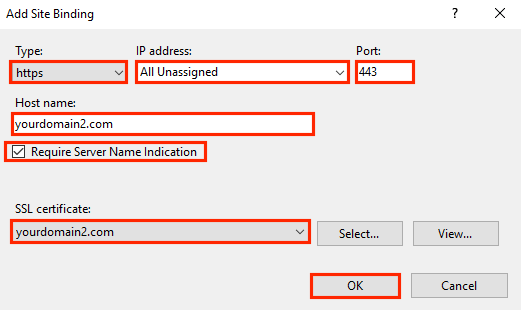
-
You have successfully assigned another SSL certificate and configured the website to accept secure connections.
Test Your Installation
To verify that the installation is correct, use our DigiCert® SSL Installation Diagnostics Tool and enter the DNS name of the site (i.e. www.yourdomain.com, or mail.yourdomain.com) that you are securing to test your SSL Certificate.
Troubleshooting
If you run into certificate errors, try repairing your certificate trust errors using DigiCert® Certificate Utility for Windows. If this does not fix the errors contact support.