
Cybercafes and libraries are perfect places to surf the Internet in a relaxed atmosphere. Unfortunately, they are also the perfect place for something else: man-in-the-middle (MITM) attacks.
An MITM Attack Is Like a Game: But They’re Playing with Your Information
An MITM attack is just like the childhood game of keep away, where two people throw a ball back and forth and a person in the middle tries to take the ball.
This childhood game is what happens in a MITM attack with a few key differences; rather than playing in a park, users are on their computer. And, instead of passing a ball back and forth, they're passing their personal information. But the biggest difference is that unlike the children with the ball, users are unaware that the MITM is trying to get their information.
Public WiFi Is a Playground for Hackers
An MITM can use various software programs to sniff Internet traffic at a cybercafe, coffee shop, library, hotel, or university to discover the IP addresses of potential victims and the WiFi router on the network.
Through ARP spoofing, the attacker can redirect the traffic to flow through their own computer before getting to the server or hotspot. In essence, the attacker's computer becomes (at least as far as the victim's computer is concerned) the WiFi hotspot.
While in this position, anything passed between the user and the router the attacker can see in plain text (usernames and passwords, credit card numbers and PINs, account numbers, and any other sensitive information).
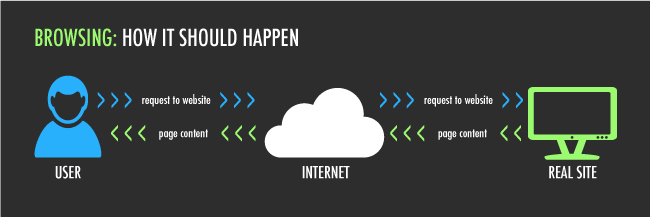
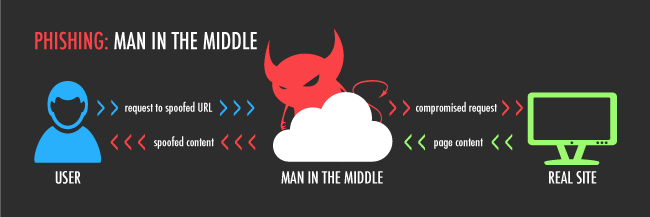
The Potential Repercussions for Man-in-the-Middle Are Huge
You can imagine what an attacker could do with your sensitive information. If an attacker intercepted your username and password while you were on a website the attacker could do anything on there without you knowing.
Once you found out that your username and password had been compromised your trust in that particular website could be irrevocably damaged. All this can be done within a few minutes, by anyone with access to the software and without you knowing that your information had been compromised.
However, as with any attack, there are ways to help prevent you and your users from becoming victims.
Tips to Prevent and Avoid MITM Attacks
Avoid sending or accessing sensitive information over an open network
Unless you are absolutely sure that you are safe, leave these types of Internet usage for a secure network.
Trust your browser
Web browsers come with a list of trusted Certificate Authorities (CA). If there is a problem with the certificate because it has expired or was not installed correctly, a warning message will pop up. Similar messages will pop up if the certificate is not trusted or if it is a self-signed certificate.
Educate users on visual cues
There are a couple visual cues admins can educate users to look for before they log in to an email or bank account. The first visual cue is the https in the address bar. The s means the site is secure. When the s is not present users should not enter sensitive information in to the website.
Pay attention to warning messages
Any keen or even not so keen Internet surfer has no doubt received the message “Do you trust this computer?” or “This Connection is Untrusted.” With so many of these messages popping up it is very easy for a user to become frustrated. Once users become frustrated they may ignore the message and continue doing what they were doing, making them vulnerable to MITM attacks.
Use EV SSL Certificates on public-facing pages
There are many benefits to using an EV SSL certificate. For example, the green browser address bar that an EV certificate provides is a better visual cue for users than the https is alone. Studies have shown that customers are more likely to purchase from a site displaying an indicator that the site is secure.
By securing your site with an EV SSL certificate you are showing you clients that you care about keeping their information safe.
DigiCert Is Working to Keep You Safe
While man-in-the-middle attacks aren't new, it's important to make sure you're taking the necessary precautions to guard against security attacks.
As an SSL Certificate provider, DigiCert is aware of the threats to your data security and is constantly working to prevent cyber criminals from accessing your data. We promote high-assurance certificates and are on the forefront of emerging markets, as demonstrated by our work with securing healthcare record transfers and using certificates to secure the Internet of Things.







