PKI: Solving the IoT Authentication Problem

Big data and connectivity are changing the way we live and do business. Connecting every day devices, products, and systems to the global Internet provides the ability to have rich data at our fingertips to improve our decision-making, analyze patterns, and, for businesses, improve the bottom line. This movement toward connecting everything to the Internet is often referred to as the Internet of Things (IoT).
Yet too often, in the rush to launch the next smart car, industrial plant, home automation system, or connected medical device, information security has been an after-thought. Making sure products work as advertised has come first. Incorporating security by design is the next step forward for the IoT, and device and system authentication is essential in order to prevent catastrophic attacks.
Public key infrastructure (PKI), most commonly thought of as a way of authenticating websites and encrypting data for e-commerce using SSL/TLS certificates, provides a scalable and flexible solution that can help secure IoT devices and systems today.
According to Gartner analysts, “Public key infrastructure (PKI) will re-emerge as one of the most relevant authentication mechanisms for organizations to address the IOT authentication problem. PKI's flexibility is important when changing requirements and represent identity in a cross-platform, multiprotocol approach . . . Gartner predicts that discovery, provisioning, authentication and data protection will account for half of all security spend in the next five years.”
Evolving Threats
The number of connected devices expected to hit the market over the next few years is on the verge of an exponential expansion. Gartner predicts that by 2020, there will be more than 25 billion IoT devices in the world—that’s approximately three connected devices for every man, woman and child living on the planet.
With this rapidly growing attack vector, new threats and vulnerabilities are emerging that threaten the IoT’s growth and even today’s way of living.
In 2008, hackers disabled a surveillance camera to a Turkish oil pipeline to shut down alarms, cut off communications and super-pressurize the pipeline without being noticed. This resulted in a massive explosion, because the teams overseeing the facility did not receive the proper notifications of a pressure buildup. More recently, we’ve seen demonstrations of infusion pump attacks, showing how a hacker could possibly gain control and change the amount of life-saving medicines being applied to a patient in care. In response to these reports, the U.S. Food and Drug Administration (FDA) recently issued warnings about insulin pump vulnerabilities and, subsequently, published draft guidance for Post-Market Management of Cybersecurity in Medical Devices.
Last year, a security firm reported that three hospitals had been breached through vulnerabilities in their medical devices ranging from MRI machines to blood gas analyzers. There was also the widely-viewed online video broadcast where security researchers took control of a Jeep and steered it into a ditch. In separate incidents, attackers hacked a smart rifle and took control of a baby monitor to speak directly to the young infant.
Though many of these are demonstrations that have yet to be carried out in the wild, it’s only a matter of time before smart hackers with bad intentions inflict major harm on businesses, communities, and nations through vulnerabilities found in connected devices and systems. That is, unless the industry pays more attention to security.
PKI offers a scalable path forward for embedding device discovery, authentication, and data encryption to protect the integrity of critical messages being sent through the IoT.
Authenticating all Things with PKI
The challenge of the IoT and the tens of billions of connected devices entering the market is one of trust. With so much data flowing across the web, it becomes critical to know who is authorized to send and receive the data. This involves providing strong authentication from devices to cloud services and for device users.
With IoT, the stakes are much higher. If information gets into the wrong hands, or if the integrity of the data in transit is altered, it could present a life-threatening situation to the patient relying on an infusion pump or pacemaker or even for the driver heading down the freeway at 70 miles per hour. Organizations must provision IoT devices and systems with trusted credentials—and do so at scale.
Enter PKI
Using an open standard for interoperability, PKI can be adapted to many use cases, across disparate protocols and platforms. PKI can scale, as opposed to more personal forms of authentication and encryption such as PGP, so that billions of IoT devices and systems can be provisioned with digital certificates that are managed in centralized locations. Providing a unique private key to each device and user constructs a secure digital tunnel through which only authorized data flows, encrypted, and outside the view of surveillance and intruders. This type of work is already being done by innovative companies. For example, Plex and DigiCert announced a partnership in June 2015 that secures tens of millions of devices and servers with TLS certificates.
This is just the beginning, as PKI is being used to secure connected medical devices, industrial systems, smart homes and cities, and many other next-generation products. While the IoT is still in development, we have time to do security right and enable these devices in a way that limits the potentially devastating consequences of faulty security.
Certificate Management for Tomorrow’s Connected Lifestyle
The IoT requires fast, scalable, and trustworthy digital certificate deployments. For those communicating via public Internet, these companies need to use publicly trusted certificate root authorities that help users know they are connecting to the authorized location on the web. Other IoT environments do not rely upon public trust, because they operate in closed systems. These networks can utilize private PKI, but they still require the sophisticated automation and certificate management that only a trusted partner can provide.
Regardless of whether public trust is needed, companies need to discover devices, provision them with trusted credentials, authenticate access to web servers and networks, and encrypt data in transit. Comprehensive digital certificate management can do this at scale.
Consider these three basic scenarios for how PKI helps protect critical IoT devices and systems today:
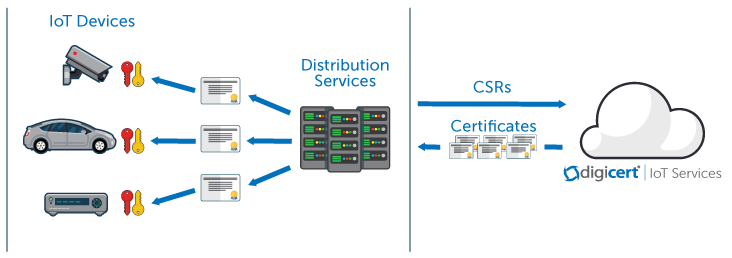
Certificate Deployment for Distribution or Platform Services
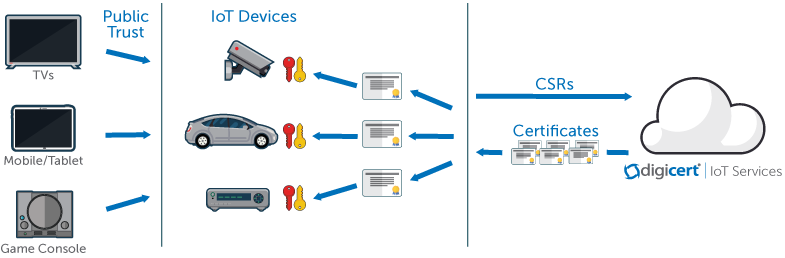
Certificate Deployment: Direct to Devices
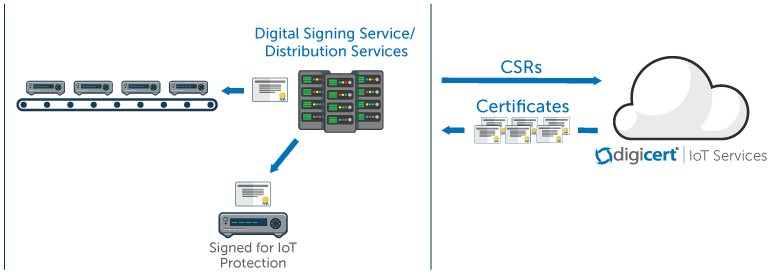
Certificate Deployment: Manufacturing Signing
DigiCert has built a modern, robust certificate management platform with the IoT in mind. This includes responsive, flexible APIs using the REST protocol, OCSP responders that serve certificate checking over the edge with CDNs for the industry’s fastest response times, and a cloud-based certificate management system that has been tested to handle billions of certificates seamlessly. The company’s advanced certificate management platform, CertCentral®, helps simplify certificate installation across IoT platforms via express install commands. Companies also gain unique insight into their certificate landscape to monitor against certificate expiration, unauthorized certificates, and to inspect for poor configurations and other gaps in best practices that could present vulnerabilities.
Don’t Wait, Use PKI Now
PKI provides the most scalable, flexible and ready-made solution to serve as online identity for the many things needing authentication in the IoT. How we harness PKI’s potential and work to embed it into IoT product development and management systems will determine how successful the IoT’s future can be.







