Overcoming the hurdles to S/MIME adoption
3 key things to look for in an S/MIME solution—and why you need one

Cyberattackers have spent the last few decades exploiting email’s security weaknesses for financial gain. And tools like artificial intelligence (AI) are making it easier than ever for criminals to pose as someone else.
A major player in the war against email fraud is Secure/Multipurpose Internet Mail Extensions (S/MIME), an internet standard that digitally signs and encrypts email messages. But despite S/MIME’s obvious benefits, many organizations have yet to adopt it as a cybersecurity solution.
Why? We’ll break down some of the reasons below, along with strategies for getting your organization on board.
But first, let’s look at how S/MIME works—and the threats it can protect against.
The dangers of unsigned, unsecured email
Every year, companies take their office workers through another round of security training. The IT security team sends out periodic phishing tests to see how easy it is to trick employees into clicking on an unfamiliar link.
Most employees know better. But many fall into the trap again and again. And when the suspicious link comes from a real attacker instead of IT, the damage to an organization is often devastating, costing an average of $4.45 million per data breach.
Spoofed emails have been masquerading as legitimate communications since the ’90s, but they’re far from the only threat. A lot can happen in the time it takes an email to leave the sender’s outbox and travel to a recipient’s inbox, like a hacker intercepting an email in transit and altering its contents.
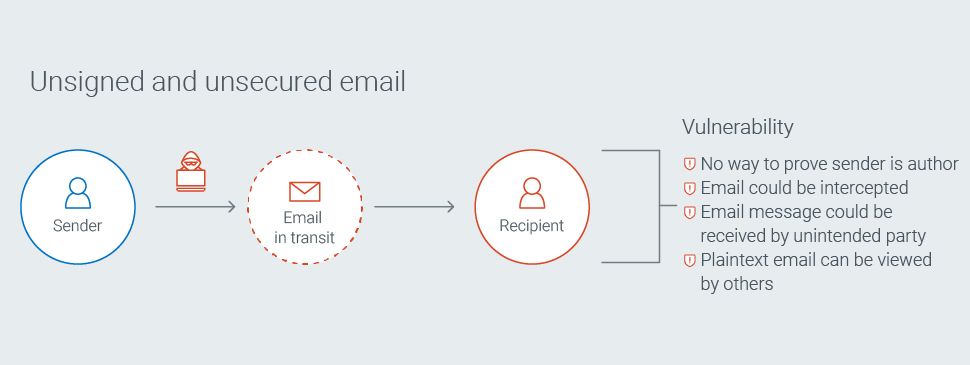
The burden falls on the recipient to figure out which email communications are real. But as attackers become more skilled at posing as employees’ trusted partners and coworkers, verifying the sender’s email address isn’t the failsafe it once was. And as tactics like spear phishing and business email compromise (BEC) grow more sophisticated, it’s becoming easier for a single misjudgment to result in the spread of malware or a catastrophic breach of confidential data.
How S/MIME secures email
When you put the burden of playing email cop on employees, you’re not just rolling the dice on security—you’re also letting spam emails distract them from the job your company is paying them to do.
S/MIME certificates remove that burden and protect the company by ensuring that the sender has been authenticated and the integrity of the message remains intact. S/MIME prevents threat actors from spoofing the sender’s address and decrypting or tampering with messages in transit.
Here’s how it works.
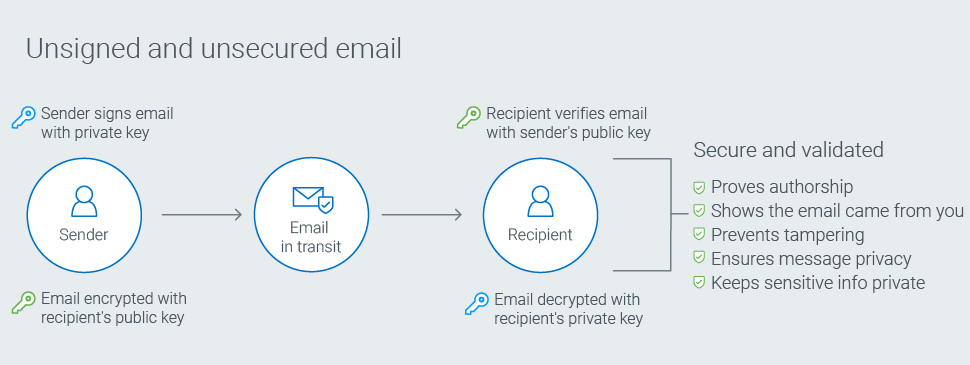
S/MIME certificates are so effective that even if the attacker were able to modify the message, it would invalidate the sender’s digital signature—an obvious way to know the message can’t be trusted.
This type of protection is a massive benefit, particularly when you consider the number of emails being sent within your organization. Using S/MIME certificates to determine whether or not a message is authentic reduces the risk across your organization while enabling employees to focus on tasks that actually benefit the business.
3 capabilities to look for in an S/MIME platform
If S/MIME solves so many of the core issues surrounding email security, why isn't it being more widely adopted? Unsurprisingly, it comes down to deployment complexities, particularly in the way S/MIME certificates are managed and scaled.
It’s the same issue organizations encounter with TLS certificates. Effectively managing a large number of certificates requires everything from discovery to the implementation of a system that automates certificate issuance to employees. You also need to be able to scale certificate use across distributed infrastructures while adhering to corporate and industry policies. As with TLS certificate lifecycle management (CLM), your S/MIME platform has to work across the entire enterprise, no matter what type of environment it’s made up of.
So what do you need from a platform to ensure you can leverage S/MIME to provide email trust at scale? Here are three capabilities to look for.
1. Central administration
First off, you need a solution that can discover, manage, and deploy all S/MIME certificates from a single console—just as you would for TLS certificates. This solution should be CA-agnostic. That means that it can see all your S/MIME certificates no matter if they were issued by a public certificate authority (CA) like DigiCert or Let's Encrypt or a private CA like Microsoft CA or DigiCert ONE CA Manager.
The ideal solution can also centralize recovery of these certificates in the cloud or anywhere else in a distributed hybrid IT infrastructure. In addition, it should give the InfoSec teams managing your public key infrastructure (PKI) a centralized way to support key escrow and recovery should user devices crash or be otherwise compromised—so there’s no anxiety about users getting locked out of their content.
2. Rapid deployment
A good S/MIME management solution lets you rapidly deploy S/MIME certificates in any environment and manage them across your organization at scale. Like TLS CLM solutions, an S/MIME management solution leverages templates with preset configurations that can be turned into profiles to automate the ways in which S/MIME certificates are configured. For example, best practices in S/MIME management dictate that separate certificates be used for digital signatures and for encryption.
In addition, users need to hold the same private key on every device where they receive email so they can decrypt communications. Automation plays an important role in deployment because it empowers IT staff to set up S/MIME without requiring employees to participate in their deployment. This rapid deployment means that when an employee joins your company, S/MIME automatically works for them from the moment they first open Microsoft Outlook.
3. Flexible autoenrollment with seamless provisioning
A good S/MIME solution should also be able to automate the provisioning of S/MIME certificates. This provisioning should include support for a wide range of enrollment and authentication methods and granular control of users, roles, and access, plus workflows with reporting capabilities and audit logs for fast remediation.
Autoenrollment is also a must. Your solution should be able to automate enrollment of certificate services for Microsoft-centric and hybrid IT environments, as well as integrate seamlessly with mobile device management (MDM) solutions. To achieve this, your solution needs to leverage PKI management solutions that integrate directly with corporate directory services to automate the installation, renewal, and revocation of certificates. This reduces the burden on IT technical support, ensures adherence to preferred security measures or corporate policy, and eliminates any provisioning or revocation gaps that can impact productivity or security.
The best S/MIME solution combines effective CLM with managed PKI
You may have noticed that an effective S/MIME management solution looks similar to platforms that manage TLS. There’s a good reason: TLS and S/MIME certificates are both x.509 certificates used as part of PKI. Since most CLM solutions don’t offer support for S/MIME, people often think of the different PKI models as separate entities.
The best S/MIME platform isn’t a standalone tool. It’s part of a unified solution for all your certificates, whether they’re TLS server certificates, TLS client certificates, S/MIME certificates, or code signing certificates, and it supports these processes across public (external) and private (internal).
With a comprehensive solution like DigiCert Trust Lifecycle Manager, your organization will have a complete digital trust platform that removes the complexity of certificate management and reduces risk across your enterprise.
The latest developments in digital trust
Want to learn more about topics like S/MIME, PKI, and certificate lifecycle management? Subscribe to the DigiCert blog to ensure you never miss a story.






