
For better or for worse, every aspect of our lives today is digitally connected – from how we socialize to where we work to even how our health devices are connected. Yet as we constantly engage online, how do we know that our footprint in the digital world is secure?
Establishing trust, particularly digital trust, is critical in the connected world and will be even more important as we move into the era of Web 3. As the internet continues to evolve, we are seeing a shift towards decentralization and the use of blockchain technology, which is leading to a greater emphasis on security and transparency.
What is Web 3?
Web 3 is the next evolution of the internet, where data is decentralized and owned by users themselves, to empower individuals, enhance security and foster trust in a peer-to-peer manner. Unlike its predecessors, Web 3 leverages blockchain, distributed ledger technologies and smart contracts to establish a transparent, verifiable and tamper-resistant digital infrastructure. It also enables users to reclaim ownership and control over their data, fostering privacy and autonomy.
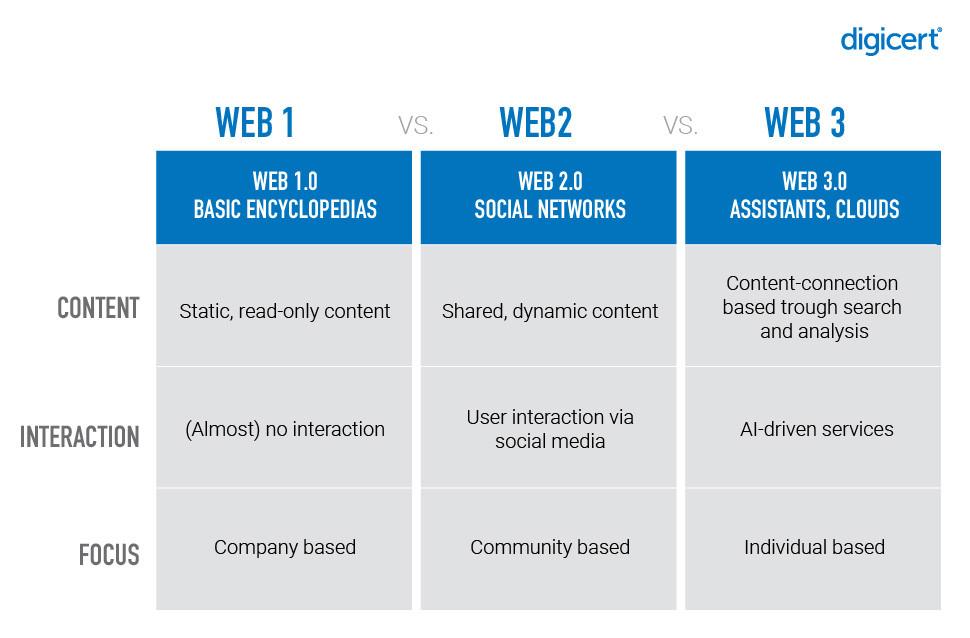
Figure 1 – Comparing Web 1, Web 2 and Web 3
We recognize the emergence of Web 3 as a groundbreaking evolution in the digital landscape. However, as a leading provider of digital trust, we also recognize that establishing confidence that online interactions are secure and valid in Web 3 will be just as critical as it is in Web 2. As the web evolves, so will threats. At DigiCert, we are interested in how we can support the secure and trustworthy implementation of Web 3 technologies, ensuring that individuals and organizations can embrace this new era of the internet with confidence.
Decentralization will increase trust
Currently, in Web 2, data is centralized, and thus users are often dependent on third parties to ensure the security and integrity of their information. We’ve seen numerous data breaches where sensitive information has been compromised, such as the high-profile Equifax breach in 2017. DigiCert has been tracking these breaches for a while now, and we share examples every month in our latest news round ups. These breaches are all too common, but there are steps companies can take to mitigate the risk of breaches occurring. However, individuals have less control over protecting their data.
On the other hand, in a decentralized system, trust is established through cryptographic methods and consensus mechanisms, rather than through centralized institutions. This means that users would have more control over their own data and are less reliant on third parties to ensure the security and integrity of their information. In this scenario, users can better protect their data and prevent identity theft and fraud. However, it also makes users more responsible for protecting their digital identity. Users will need to be careful in securing their data, securely storing private keys and following security best practices.
The blockchain will increase security and transparency
The use of blockchain technology will also play a key role in the establishment of digital trust in Web 3. On the blockchain, transactions are recorded immutably so they cannot be changed or destroyed by third parties. Blockchain is a distributed ledger technology that allows for transparent and secure transactions. Each transaction is recorded in a block, which is then added to a chain of blocks, creating an immutable record of all transactions. This makes it extremely difficult for anyone to tamper with the data, as any changes would be immediately apparent to all users of the blockchain. This transparency and security make blockchain a candidate for building trust among users.
As the web evolves, so will attackers
As we’ve seen over the past several decades of Web 1 and Web 2, motivated parties will find ways to exploit any vulnerabilities present. This applies to Web 3 as well, as attackers have already started attacking technologies on the blockchain. Notably, as the number of people investing in cryptocurrency continues to grow, it becomes increasingly lucrative for attackers. Since 2012, almost $3 billion has been stolen from crypto exchanges, and there have been approximately a dozen attacks since the start of the pandemic, resulting in a loss of over half a billion dollars since April 2020. The methods of stealing cryptocurrency are varied, ranging from stealing or guessing passwords to hacking exchange platforms, as well as phishing attempts. The most common attack method is stealing private keys from a crypto wallet. Although it may not be possible to be completely secure against all types of attacks, there are several steps that can be taken to secure cryptocurrency and reduce the level of risk. We shared them in a previous blog here.
Digital trust is the new standard
In summary, Web 3 has the potential to offer more trust, transparency and security, while allowing users to have greater control over their personal information and digital identities. Digital trust is a fundamental aspect of securing online interactions, in Web 2 and beyond. Moving further into the era of Web 3, it is important that we continue to focus on digital trust as we work towards a more secure and transparent internet.





