Fix for an Expired Intermediate SSL Certificate Chain

June 2020 Update: With a large number of sites affected by the recent expiring of a root certificate, we thought it would be valuable to again share this guide on intermediate TLS/SSL certificates in the certificate chain. Note that intermediate certificates rely on root certificates. For more information on root certificates, read The Impacts of Root Certificate Expiration.
Orignal 2014 Content
On July 26, 2014 at 12:15 PM, some customers and users on sites secured by DigiCert reported that they were getting an untrusted certificate error.
The problem is related to a locally installed legacy intermediate certificate that is no longer used and no longer required for the certificate installation. The problem can affect any client platform with a locally cached or installed intermediate certificate.
So far we've seen the issue happen with:
- Clients (mainly OS X) with the expired intermediate installed in their local keychain.
- Server-to-server connections on Windows environments, where one server still has the legacy certificate installed.
Expired Legacy Intermediate Certificate
The expired certificate in question is the “DigiCert High Assurance EV Root CA" [Expiration July 26, 2014] certificate. This temporary intermediate certificate was used in years past as part of a compatibility chain for older devices.
This certificate has not been used for over three years and is unnecessary for installations.
From additional information, users affected appear to have the expired intermediate in the ‘login’ keychain or stored locally on their server or in have the expired intermediate installed on a backend server or application.
Fixing the expired intermediate certificate on Mac OS X
The errors on Mac OS X are due to a locally installed intermediate certificate in the login keychain.
OS X users can resolve the issue by deleting the certificate from their Login keystore using Keychain Access.
In Keychain Access go to View -> Show Expired Certs and search for 'DigiCert High" to find the DigiCert High Assurance EV Root CA that expired on July 26, 2014. Delete this certificate and close Keychain Access.
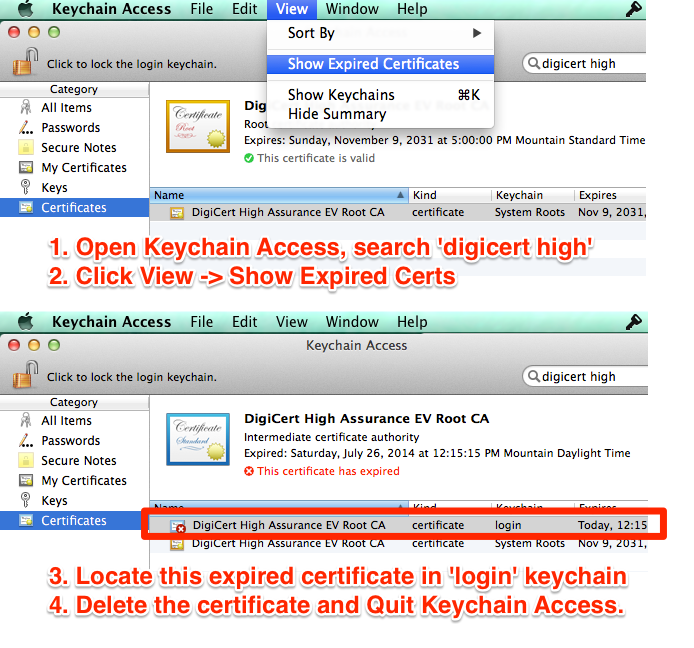
(Credit to Allen Hancock @yesthatallen for the solution in picture form and others who jumped in with responses)
Repair Intermediate Certificate on Windows, Exchange, ISA, TMG, Lync
Administrators running Windows/Exchange with an ISA server or TMG can run the DigiCert SSL Installation Diagnostics Tool.
Affected servers will produce the warning, "Your server is not sending the right intermediate certificates." On Windows servers, this can be resolved using the DigiCert Utility.
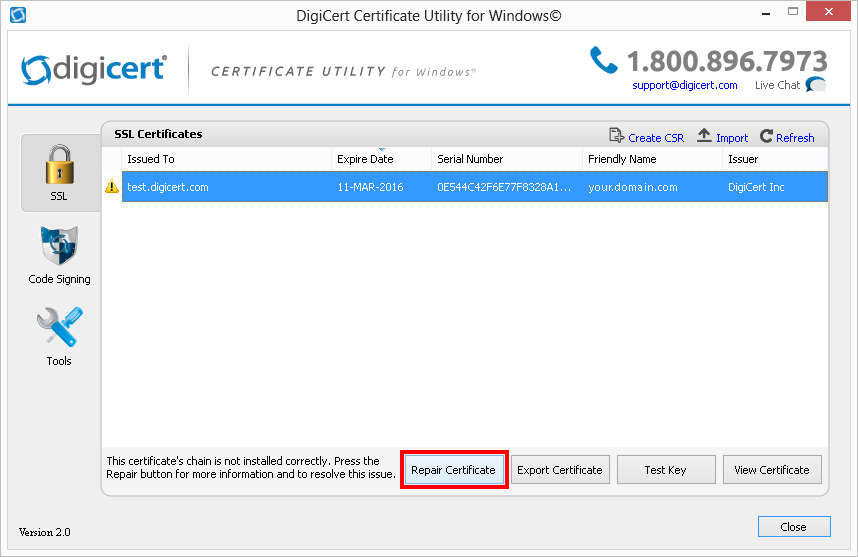
When the Utility runs on your server, a warning may appear. Click “Action Required” and “OK” to delete the expired intermediate and enable the correct certificate chain. The server will most likely need to reboot for the change to take effect.
If you are unable to run the utility, you can manually delete the DigiCert High Assurance EV Root CA certificate expiring on July 26, 2014 to resolve this issue. You do not need to reissue your certificate.
Fixing the expired intermediate certificate on Apache
Administrators on Apache, can replace the SSLCertificateChainFile with the correct DigiCertCA.crt provided with the certificate received from DigiCert, which may downloads from your DigiCert account under your order details.
No action required for most certificate installations
All current installations of certificates issued by DigiCert include the most up-to-date intermediates in order to establish trust with browsers.
But administrators who received the notifications from DigiCert should remove the expired legacy intermediate from their server to avoid any potential conflicts.
If you have details on other affected platforms, please contact support so we can get additional details and update our documentation for other users to resolve the cached intermediate error.
If you need assistance with this or any other issues, our support team is always happy to help.







