
The Industrial Internet of Things (IIoT) spans a wide range of smart sensors and networked devices, providing data and analytics that enable manufacturers to improve efficiency and increase reliability.
But each stage of a device’s lifecycle—from design and development to manufacturing and deployment—presents its own set of security challenges that, if neglected, can expose vulnerabilities and lead to serious breaches.
As IIoT devices become more and more integrated into critical industrial processes, more targets open up for cyberattacks. And without a comprehensive security approach, a single vulnerable device can jeopardize an entire network.
Let's look at the four essential steps for safeguarding IIoT devices from start to finish.
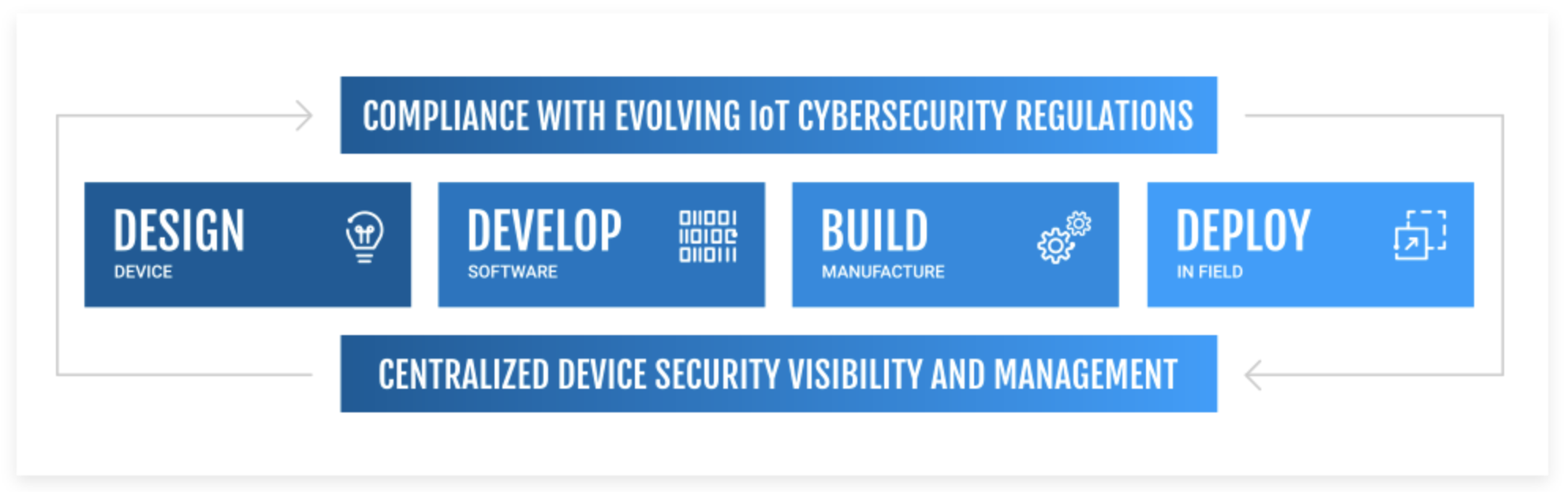
1. Design: Building security from the ground up
The journey toward IIoT device security begins during the design phase. To make sure you’re arming devices against threats right from the start, these security features should be embedded early in the development process:
- Crypto-agility and compliance: Achieve crypto-agility by integrating flexible cryptographic algorithms that can adapt as threats evolve, ensuring compliance with industry standards.
- Secure hardware integrations: Protect cryptographic keys and sensitive data from tampering by designing devices with built-in hardware security elements, like trusted platform modules (TPMs) and secure elements.
- Adherence to industry standards: Follow established guidelines like IEC 62443 or NIST to ensure you’re incorporating security best practices from day one.
2. Develop: Creating secure software foundations
Proper software development practices help prevent IIoT vulnerabilities that attackers could exploit once devices are deployed.
- Software vulnerability scanning: Integrate automated tools that scan for vulnerabilities during the software development lifecycle, reducing the chances of flaws making it through to production.
- Validated software signing: Implement code-signing processes to validate the integrity and authenticity of the software, ensuring that the only code executed on the device has been verified.
- Secure coding practices: Employ secure coding standards to minimize the introduction of vulnerabilities and conduct rigorous testing to detect and remediate issues early.
3. Build: Manufacturing with security in mind
The build phase is where devices are physically manufactured. To prevent tampering and counterfeit devices, upholding security measures during this stage is a must.
- Hardware-backed identities: Equipping devices with cryptographic identities stored in hardware ensures authenticity and protects them from unauthorized access.
- Certificate distribution and management: Securely distribute and manage certificates during manufacturing to establish device trust and enable secure communications.
- Counterfeit prevention: Use robust supply chain security measures to prevent counterfeit components and ensure that only legitimate devices are produced and deployed.
4. Deploy: Configuring and securing devices in the field
Deployment involves not just connecting devices to the network but ensuring they’re configured securely and monitored continuously.
- Zero-Touch provisioning: Simplify the onboarding of devices through automated provisioning processes that securely connect devices to the network without manual intervention.
- Secure software updates: Maintain device integrity by regularly updating firmware and software to patch vulnerabilities and add new security features.
- Continuous threat monitoring: Implement monitoring systems that provide real-time insights into device behavior, quickly identifying and mitigating threats as they emerge.
Make a continuous commitment to IIoT security
You can see why taking a comprehensive approach to IIoT device lifecycle security is so important. By embedding security from design to deployment, you can greatly reduce your organization’s risk exposure while maintaining compliance and ensuring your industrial operations remain resilient.
DigiCert Device Trust Manager makes it easy to build strong security and updating capabilities right into your IIoT devices. Our solutions can help you protect your devices at every stage, managing device identity, securing connections, preventing device tampering, and updating firmware remotely and securely—all the makings of a device that remains secure from birth to end of life.
Talk to an expert today to learn how DigiCert Device Trust Manager can help you secure your IIoT environment.
The latest developments in digital trust
Want to learn more about topics like device trust, crypto-agility, or the Internet of Things? Subscribe to the DigiCert blog to ensure you never miss a story.






